Permissions Tab for Equipment Classes
On the Permissions tab for an equipment class (shown below), you can identify the runtime users and/or groups that can access the equipment node in the asset tree, and you can even limit the runtime menu commands that users and/or groups can access for the equipment node. Equipment nodes created using this equipment class will have these permissions defined for them at the time they are initially created.
Equipment Class Form - Showing the Permissions Tab
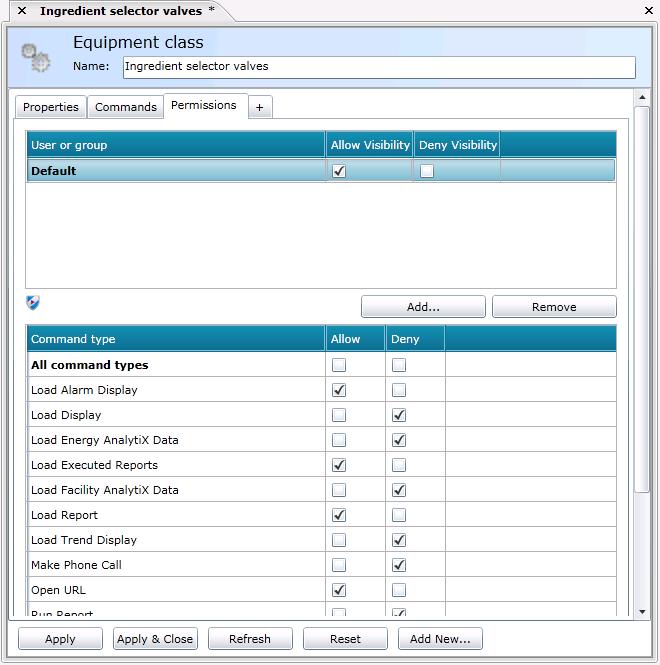
To open the Permissions sub-tab, in the Project Explorer, click the AssetWorX provider button to open AssetWorX. Then in the navigation tree, expand localhost > AnalytiX Catalog configuration > Equipment Classes. Navigate to the equipment class you are entering properties for and click on it. This displays the Equipment Class tab; click on its Permissions sub-tab. Use this tab to define the users and groups that can access the equipment node and commands. Each prompt on this sub-tab is described below.
Options on the Permissions sub-tab are described below:
-
User or Group table: Use this table to allow or deny visibility of the equipment node to specified users and/or user groups. Default identifies permissions for all users and groups that are not specifically included in the table. To override the default permissions for a specific user or group, you must first add the user or group to the table by clicking the Add button and then navigating the security server to find the user or group to be added. Permissions work as follows:
-
-
In order for the equipment to be visible to any user or group, all of the equipment's parent nodes must be visible to that user or group.
-
Initially, the Default user settings for the Allow Visibility and Deny Visibility check boxes are both empty. When BOTH check boxes are empty, the equipment node inherits the permissions defined for its parent equipment node.
-
By putting a check mark in the Default user's Allow Visibility or Deny Visibility check box you break the node's inheritance of permissions and define the settings for all users not listed in the table. A check mark in the Allow Visibility check box lets the Default user (all users and groups) see the node in the runtime asset tree, but a check mark in the Deny Visibility check box prevents the Default user (all users and groups) from seeing the node in the runtime asset tree.
-
The following sequence determines whether a user does or doesn't have visibility to an equipment node:
-
-
Where a user is a member of a group, the Deny Visibility setting takes precedence over the Allow Visibility setting. This means that if permission is denied for a group, all users in the group are denied (even if settings for one of those users allows visibility).
-
If the permission cannot be determined, the permissions setting for the Default user (all users and groups) is used.
-
If there is neither a Deny nor an Allow for the Default user, the parent equipment node's permissions are used.
-
If there is no parent, the equipment node is visible.
-
Command Type table: This table is populated only when a user or group is selected in the User or Group table. Use this table to allow or deny access to the equipment node's runtime right-click menu items for the selected user. Runtime right-click menu items are defined for the equipment node using the Commands tab; for a description of each type of command, refer to the Commands tab for Equipment topic. Permissions for command types work like this:
-
-
By default, no command types are selected; the user has permission to access all command types.
-
You can Allow or Deny access to All Command Types or individual command types. Note that if there are multiple commands defined for a command type, then permission is allowed or denied for all runtime menu items that use that command. For example, if five menu items load reports using the Load Report command, permission to allow the Load Report command allows all five reports; you cannot give permission to only three of the five reports.
See also:
Overview of Equipment Classes (Templates)
Defining User and Group Permissions for Equipment
![]()
