Use Global Settings to set polices that control how the GENESIS64 Security Server maintains accounts in its database. You can also identify critical points and alarms in your database that cannot be written to without user authorization.
To access global settings, right-click Global Settings as shown in the figure below then select Edit or Edit on New Tab. The Global Settings form appears with its three tabs: General, Critical Points, and Critical Alarms. Each tab is describe below in this topic.
Edit Global Settings

Global Settings General tab (shown below) provides access to the polices that control how the GENESIS64 Security Server maintains accounts in its database. You can choose to have the Security Server interact with the Windows domain services and provide the connection to the correct domain, how the account user name in the ICONICS security database maps to the Windows domain account, and provide the necessary domain credentials so that GENESIS64 can accept pass-through authorization from the Windows domain.
You can set a policy that will accept the current Windows user account credentials, populate the login dialog with domain users, and change the security mode. Settings maintained in the Security Server database are the automatically synchronized with the domain service.
General Settings
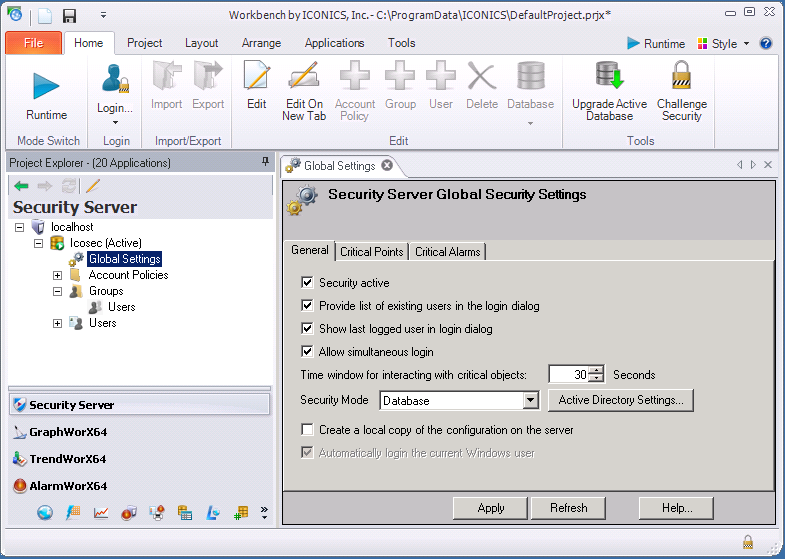
The following properties may be set on the General tab:
Security active. Putting a check mark here means that general security will be applied. Removing the check mark means that it will not be applied.
Provide list of existing users in the login dialog. When this box is checked, the Security Login dialog box displays a list of all users in the User Name drop-down list. This option is often desirable for touch-screen systems.
Show last logged user in login dialog. When this box is checked, the Security Login dialog box displays the name of the last user that successfully logged in the User Name field.
Time window for interacting with critical objects. Amount of time (in seconds) after logging in that a user will be allowed to manipulate a critical point before being required to log in again.
Security Mode. You can select either to authenticate using the ICONICS Security Server database or using the Active Directory.
Only one Windows domain can be used to authenticate users if you choose to use the Active Directory synchronization feature. This feature eliminates the need for users who have already logged into an Windows domain to enter a user name and password a second time to gain access to the Security Server through the Security Login application. This feature, commonly referred to as "single sign-on," is available in all security modes (i.e., basic, advanced, and integrated NT). (Default is off.)
To specify Windows domain authentication:
Select Active Directory in the Security Mode list box.
Click the Active Directory Settings button to view the Active Directory Settings dialog box shown below.
Enter the domain name into the Domain name text field.
Select the system used to map the user name, either sAMAccountName or userPrincipleName, from the Map username drop-down list box.
The sAMAccountName is the name of the Windows account in the domain. The userPrincipleName is the Internet login style based on the RFC 822 standard, and is typically an e-mail address in the form username@domain.com.
Active Directory Settings Dialog Box
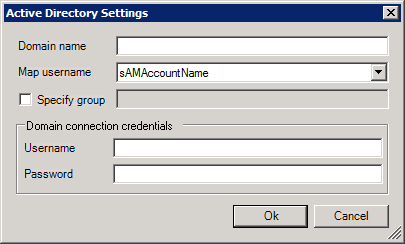
Enter the Domain connection credentials for the administrator of the domain in the form of the administrator's user name and password in the Username and Password text fields.
Click OK.
On the Critical Points tab of Global Settings, shown in the figure below, you can designate a subset of write-able points (OPC data items) known as critical points. When writing a new value to a critical point, the user will be prompted to login again immediately before writing a new value. This ensures that the person writing the value is an authenticated user.
Critical Points Settings
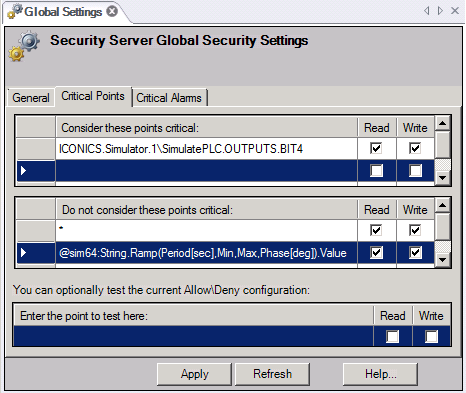
You can use wild cards as part of the point name. This lets you specify multiple tags without listing them individually. For details about how to do this, refer to Wildcards and Performance Optimization.
In order for a user to write a new value to a critical point, the following two conditions must be met:
The user must be granted rights to the point via his or her user configuration or via one of the explicit groups he or she belongs to. (Rights cannot be granted from the default group).
The user must have logged in within the past Time window for interacting with critical objects period (configured on the Policy tab of Global Settings). If condition 1 is met, but not condition 2, the client application (e.g., GraphWorX64) will open a Security Login dialog box, requiring the user to log again and satisfy condition 2.
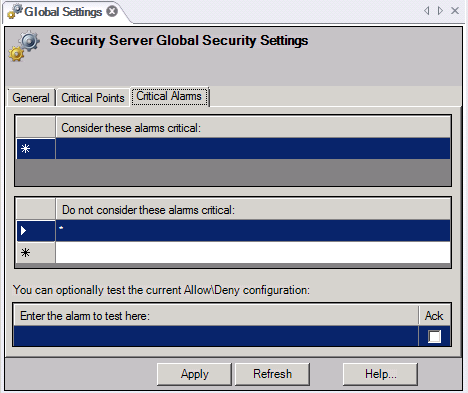
On the Critical Alarms tab of Global Settings, shown in the figure below, you can designate a set of critical alarms. When writing a new value to a critical alarm, the user will be prompted to log in before acknowledging an alarm. This ensures that the person acknowledging the alarm is an authenticated user. For more information, refer to Alarm Acknowledgement.
You can use wild cards as part of the point name. This lets you specify multiple tags without listing them individually. For details about how to do this, refer to Wildcards and Performance Optimization.
Critical Alarms Settings
See also: